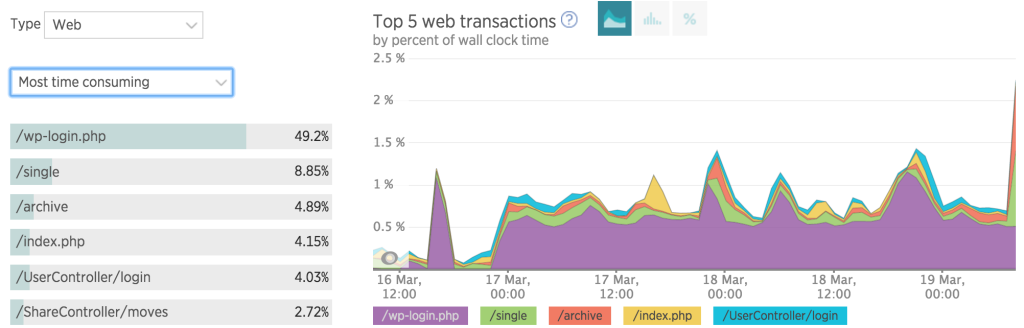
I recently added New Relic server monitoring APM to my server and I noticed something interesting. Look at the screenshot below all the purple in the graph just shows that someone is brute-forcing my login. It is burning my much needed resources for other apps on the box with multiple posts on wp-login.php
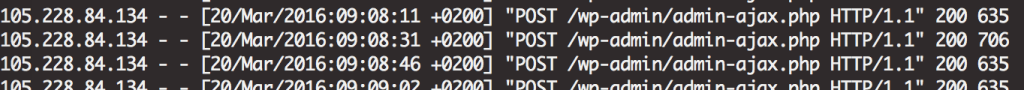
I needed to ensure this was legit so I took a look at my server access log and sure enough, multple posts to wp-login.php. I also noticed that they were also hitting admin-ajax.php. So unlikely this is a legit search engine bot and why would I want a bot to hit the admin section anyway.
I think admin-ajax.php is used for the wordpress API.
Came across this blog post that suggests using HTTP Basic Auth to protect from brute force attacks.
To summarise that if you are creating a new .htpasswd use the -c:
sudo htpasswd -c /etc/apache2/.htpasswd username
You will then type the password
Then in your virtualhost config:
<DirectoryMatch ^.*/wp-admin/>
AuthType Basic
AuthName "Restricted"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
</DirectoryMatch>Remember valid-user is the actual text that must appear, as the usernames are in your .htpasswd file.
I have just implemented this, I will let you know of the results…
WordPress Multiple posts on wp-login.php Results:
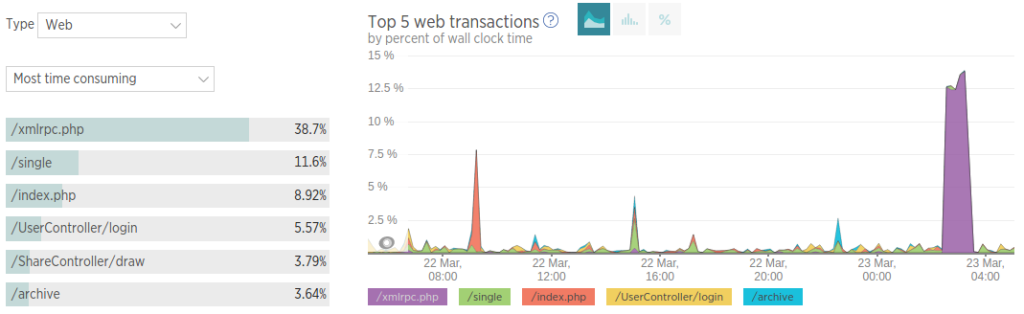
Introducing the XML-RPC Attack
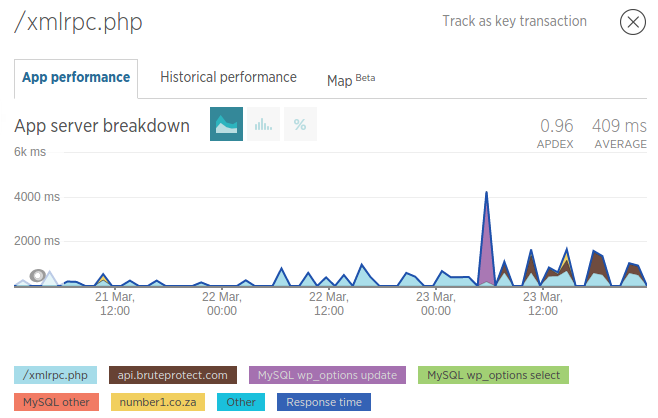
I continued to monitor the site and realised that the site was getting a lot of POST data to /xmlrpc.php
Here is some of the data I found with newrelic:
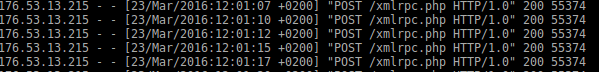
Here is some data from the access log, you can get it with:
grep xmlrpc access.log
Solving the Xmlrpc issue
There is a good link from digitalocean on protecting your wordpress from the xmlrpc attack.
Basically it says you should install Jetpack and that is what I did. I await the results….A strange thing is that fail2ban did not block the ip…I guess fail2ban is not setup to watch the access logs. There is a tutorial on that here but I’m skipping that if Jetpack works.
Results of the Xmlrpc issue
Now whenever there is a supposed xmlrpc attack, there seems to be a lot of querying to api.bruteforceprotect.com, which is what jetpack uses to check whether it really is a bruteforce attack. The problem is that the attacks now look to be happening more frequently. Will update in a few days…
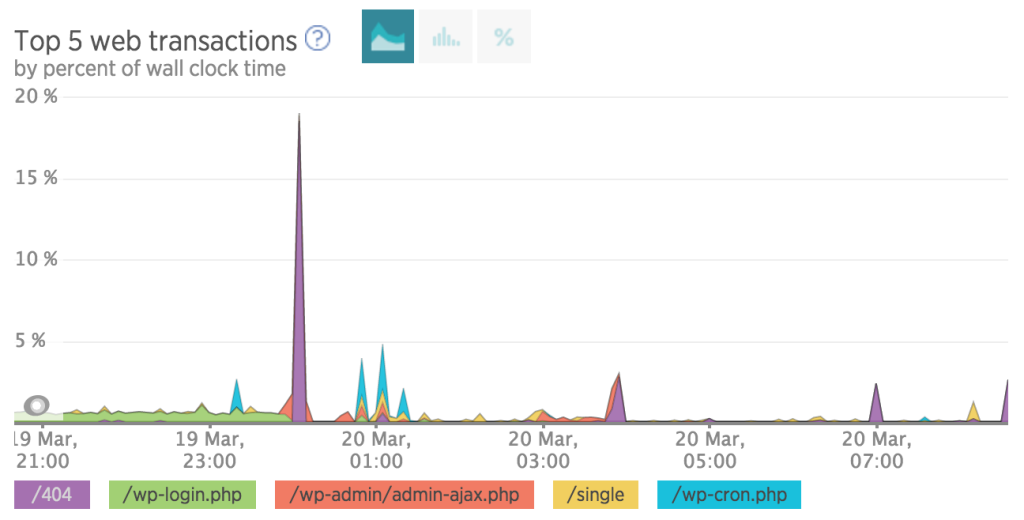
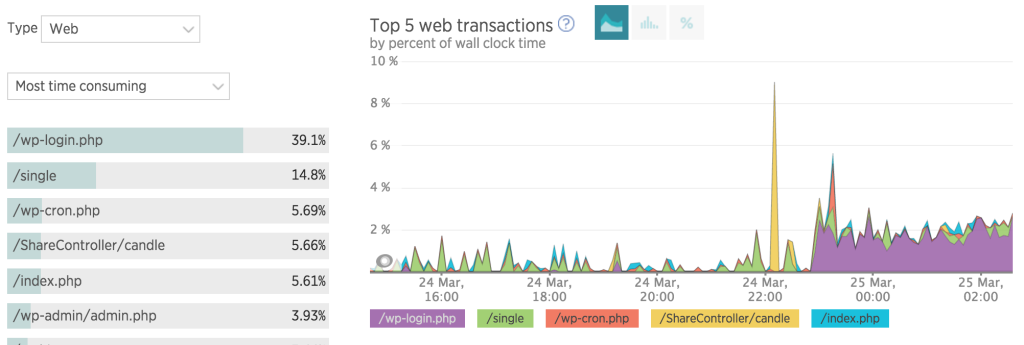
Wasn’t really blocking multiple posts on wp-login.php
So it turns out I wasnt blocking wp-login.php as it was in the root of the wordpress directory. I was still getting issues from newrelic (see the purple below)…
So to fix this issue or multiple posts on wp-login I added basic authentication to that file as well:
<Files wp-login.php>
AuthUserFile /etc/apache2/.htpasswd
AuthName "Do it! do it. do it."
AuthType Basic
Require valid-user
</Files>