So you have setup OpenShift Container Platform and try to deploy your first image, dockerhub’s nginx image and what do we get…an error:
2019/10/03 06:39:24 [warn] 1#1: the "user" directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
nginx: [warn] the "user" directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:2
2019/10/03 06:39:24 [emerg] 1#1: mkdir() "/var/cache/nginx/client_temp" failed (13: Permission denied)
nginx: [emerg] mkdir() "/var/cache/nginx/client_temp" failed (13: Permission denied)
The reality is that you are being forced to run as an arbitrary user ID and that means that some container images may not run out of the box in OpenShift
This will be the case where images do not adopt security best practices and need to be run as the root user ID even though they have no actual requirement to run as root. Even an image which has been setup to run as a fixed user ID which isn’t root may not work – Openshift cookbook
A massive blow to developer experience coming from using standard vanilla Kubernetes or RKE (Rancher Kubernetes Distro).
This is a very important consideration and the people at Red Hat Openshift have taken a stand against unnecessarily running containers as root. From what I have read kubernetes and docker swarm don’t care, they will run your root container.
It is best to read what Openshift says about support for arbitrary ID’s.
By default, OpenShift Container Platform runs containers using an arbitrarily assigned user ID.
For an image to support running as an arbitrary user, directories and files that may be written to by processes in the image should be owned by the root group and be read/writable by that group. Files to be executed should also have group execute permissions.
So to get it working you do the following to the directory being written to:
RUN chgrp -R 0 /some/directory && \
chmod -R g=u /some/directory
Remember we are talking root group not root user.
The root group does not have any special permissions (unlike the root user) so there are no security concerns with this arrangement
There is also a concern where an associated entry in /etc/passwd is required.
Lastly, the final USER declaration in the Dockerfile should specify the user ID (numeric value) and not the user name
If the image does not specify a USER, it inherits the USER from the parent image
You can allow containers to run as the root user in the configuration of Openshift Container Platform.
Check this Example Dockerfile to build your image. It seems as though you will be building your container specifically to fit into OKD’s paradigm.
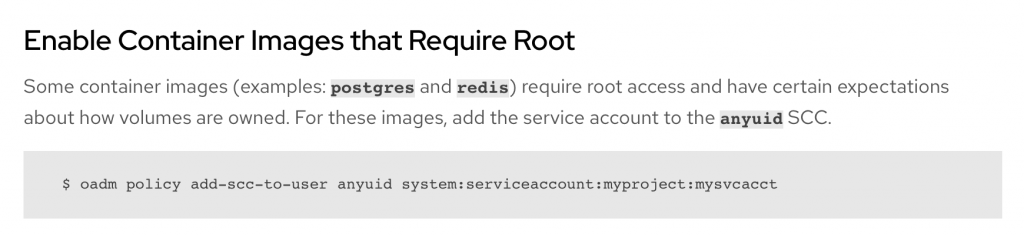
Some containers require root – and can’t get around it, so in this case an admin will have to enable those accounts. These seem to be data stores though.
Openshift ignores the USER directive of the Dockerfile and launches the container with a random UUID
What are Non-root Containers?
By default, Docker containers are run as root users. This means that you can do whatever you want in your container, such as install system packages, edit configuration files, bind privilege ports, adjust permissions, create system users and groups, access networking information.
It is also important to note that the processes running in the container cannot listen on privileged ports: So all ports below 1024.
How to Run Nginx in Open Shift?
Sources:
- Karma Computing: Building Non-root Docker images for Openshift
- Linux.com: Non-root containers Openshift
- Bitnami: Running Non-root Containers in OpenShift
- Openshift Container Specific Guidelines
- Root containers and Vulnerabilities
- Non-root containers advantages and disadvantages
- How to run nginx in openshift