The documentation for setting up an OpenIDC identity provider / authentication method for Harbor Registry can be found in the harbor docs.
Harbor has supported OIDC since version 1.8.
Importantly:
You can change the authentication mode from database to OIDC only if no local users have been added to the database. If there is at least one user other than admin in the Harbor database, you cannot change the authentication mode.
So if you have existing local users, you will need to remove them – unfortunately doing this from the admin frontend does not actually delete them. you have to enter the postgres db and delete associated projects and then the users.
Information for setting up the client on keycloak side can be found on the red hat docs page
Getting Started
Having said all that…
-
As Admin, go to
Administration -> Configuration -> Authentication -
Select Auth mode as
OIDC -
Fill in the required information as per the below screenshot:
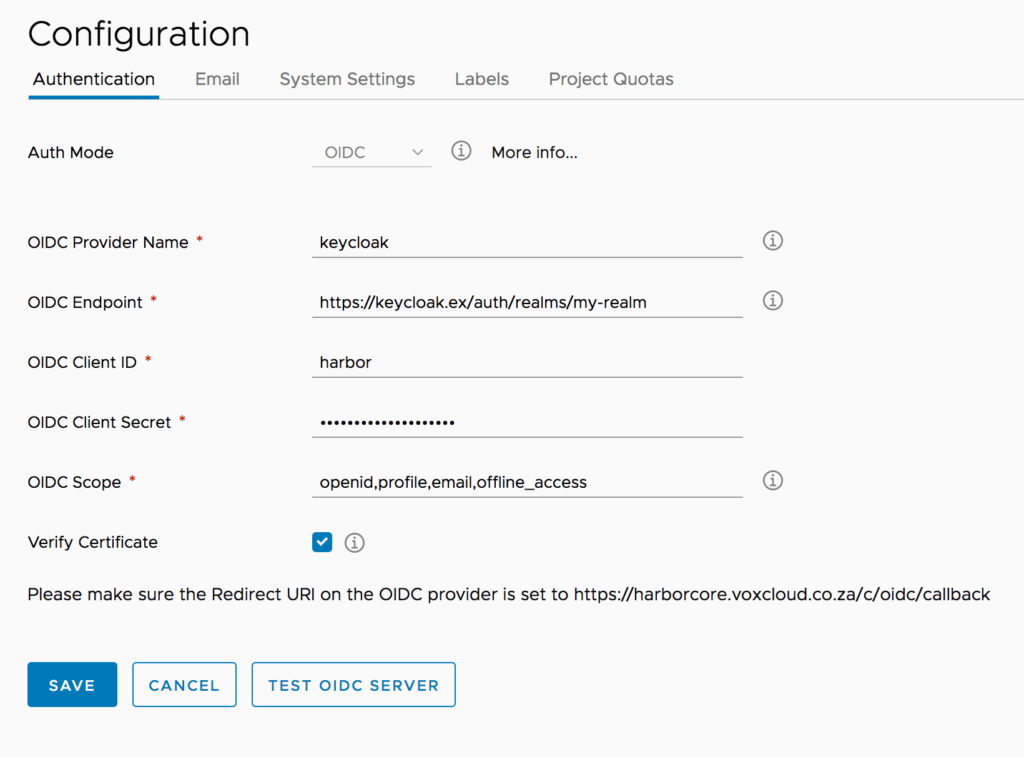
-
Click Test Configuration
OIDC Endpoint
For keycloak you can get your realm’s OIDC details by going to:
https:///auth/realms//.well-known/openid-configuration But for the OIDC configuration you remove everthing up to /.well-known... including the back slash.
So the OIDC endpoint should be:
https:///auth/realms/ Deleting Existing Harbor Users
If you are using harbor on kubernetes – you can enter the postgres pod and execute in the shell:
docker exec -it harbor-db bash
psql -U postgres
\c registry
select * from harbor_user
delete from harbor_user where user_id > 2Source
- Keycloak OIDC Endpoint github issue, thanks to Daniel Jiang for the fix.